Computer hacking Scams
What is computer hacking:
Computer hacking is the act of gaining unauthorized access to a local or remote computer by bypassing passwords and other security measures. It involves techniques used to break authentication systems, hack into internet users' accounts, computer databases, software programs, and more—primarily to exploit or compromise the privacy and security of a network.
Computer hacking scams involve fraudulent activities in which scammers gain unauthorized access to individuals' or organizations' computer systems for various malicious purposes. These scams often appear in the form of phishing emails, malware attacks, or other deceptive tactics designed to exploit security vulnerabilities. In phishing schemes, scammers impersonate trusted entities to trick individuals into disclosing sensitive information such as usernames and passwords. Malware attacks involve installing malicious software on a victim’s computer, allowing hackers to steal data, monitor activity, or disrupt operations. To avoid falling victim to computer hacking scams, individuals and organizations should adopt strong cybersecurity practices. This includes using strong and unique passwords, regularly updating software and operating systems, and being cautious of unsolicited emails, links, or attachments. Staying informed about emerging cybersecurity threats and using reputable security software are also essential steps in reducing the risk of hacking-related fraud.

Hacking computer through a phone call:
The well-known technique the scammer highly uses to trick people in hacking their computer details is by contacting through a phone call.
The scammer randomly calls any number and poses as a technical person from a big company like Microsoft. Through some registered authentication, they claim they have found a suspicious virus that has attacked your computer. If not resolved, it could delete all the details in your computer and slow down the process. If the user gets convinced and responds, then they try to catch you in the trap.
The crook asks for your computer access data, through which they easily hack your computer. Once gaining access, the scammer may change your settings, making it more vulnerable. The scammer will enroll you in some costly online program which is completely useless. They trick you into installing malware that tracks your personal information and other banking and transaction details.
While hacking a computer directly through a phone call is uncommon, scams involving social engineering through phone calls can compromise computer security. In such scenarios, scammers may pose as tech support agents or authoritative figures, claiming there's a security issue with the victim's computer. They manipulate individuals into following instructions that grant remote access or lead to the installation of malicious software. Victims, believing they are addressing a legitimate concern, inadvertently provide access to sensitive information. To protect against these scams, it's crucial to verify the caller's identity, never grant remote access or share personal information during unsolicited calls, and hang up if the conversation feels suspicious. Staying informed about common scams and maintaining a skeptical approach to unexpected calls contributes to overall cybersecurity.


Computer hacking by passing malwares:
On clicking those suspicious links, some software will get downloaded to your system. This compromises the transparency of your actions on the computer. Through this, the scammer gains complete control of your computer and misleads you in various ways. Mostly, they focus on obtaining your credit card details and passwor
What to do if you found your computer is been hacked?
-
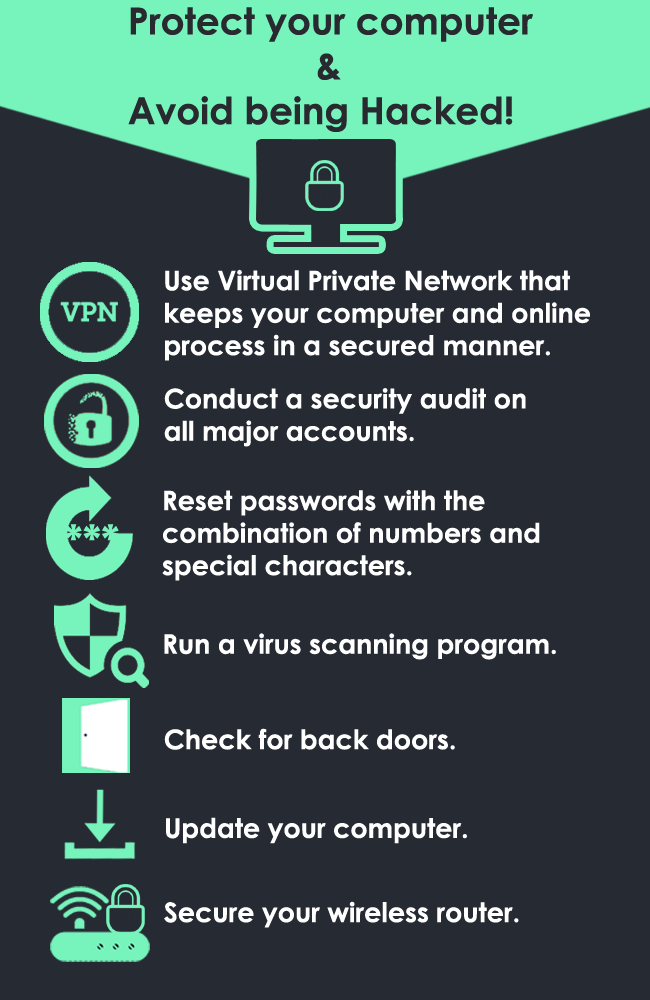
Use a Virtual Private Network that keeps your computer and online processes secure.
Conduct a security audit on all major accounts.
Reset passwords using a combination of numbers and special characters.
Run a virus scanning program.
Check for back doors.
Update your computer.
Secure your wireless router.
Ask yourself why you were hacked.
What to do if you found your computer is been hacked?
2. If the victim wants to link the complaint to any governmental sites we provide the easy get through access.
3. Regular alerts and information are posted on the latest computer hacking techniques in order to keep user cautious.
4. Through efficient filtering algorithms we get back to you the originality of URL whether it is authenticated or a malware.